
Are you investing or spending on cybersecurity?
How much is enough? How do you know?
Let us show you.
Many organizations struggle with assessing their cybersecurity posture, leading to gaps in risk management, compliance, and resilience. Without a structured benchmark, businesses often lack visibility into their security weaknesses, making it difficult to prioritize improvements and align cybersecurity with business objectives.
Cyber threats continue to evolve, and without continuous benchmarking, organizations risk falling behind industry standards, leaving their defenses exposed to modern attack tactics and vulnerabilities.
Key challenges include overconfidence in security readiness, where companies assume they have adequate protections without measurable proof. This leads to inconsistent cybersecurity investments, where budgets are allocated without a clear understanding of ROI, threat mitigation impact, or emerging security gaps.
Additionally, many organizations struggle with measuring progress against industry standards, making it difficult to justify cybersecurity spending to stakeholders. Resource constraints further complicate security planning, as businesses must balance cybersecurity investments with operational efficiency.
How do you know when your cybersecurity spending is enough? Knowledge is power, and without structured benchmarking, organizations cannot determine whether they are investing at the right level compared to their industry peers.

CyTech’s Cyber Maturity Benchmark helps businesses assess their cybersecurity posture, optimize investments, and align security strategies with industry standards.
Many organizations struggle with visibility into their security weaknesses, leading to overconfidence, inconsistent spending, and difficulty measuring progress.
CyTech’s structured benchmarking framework provides comparative insights, allowing businesses to evaluate their security capabilities against industry peers and prioritize improvements.
By leveraging AQUILA’s automated analytics, CyTech enables organizations to track security maturity, measure ROI on cybersecurity investments, and ensure compliance with evolving regulations. Their risk-based approach helps businesses determine how much cybersecurity is enough, ensuring they invest strategically rather than reactively.
With real-time benchmarking, companies gain control over their cybersecurity spending, ensuring optimized protection, regulatory compliance, and long-term resilience.
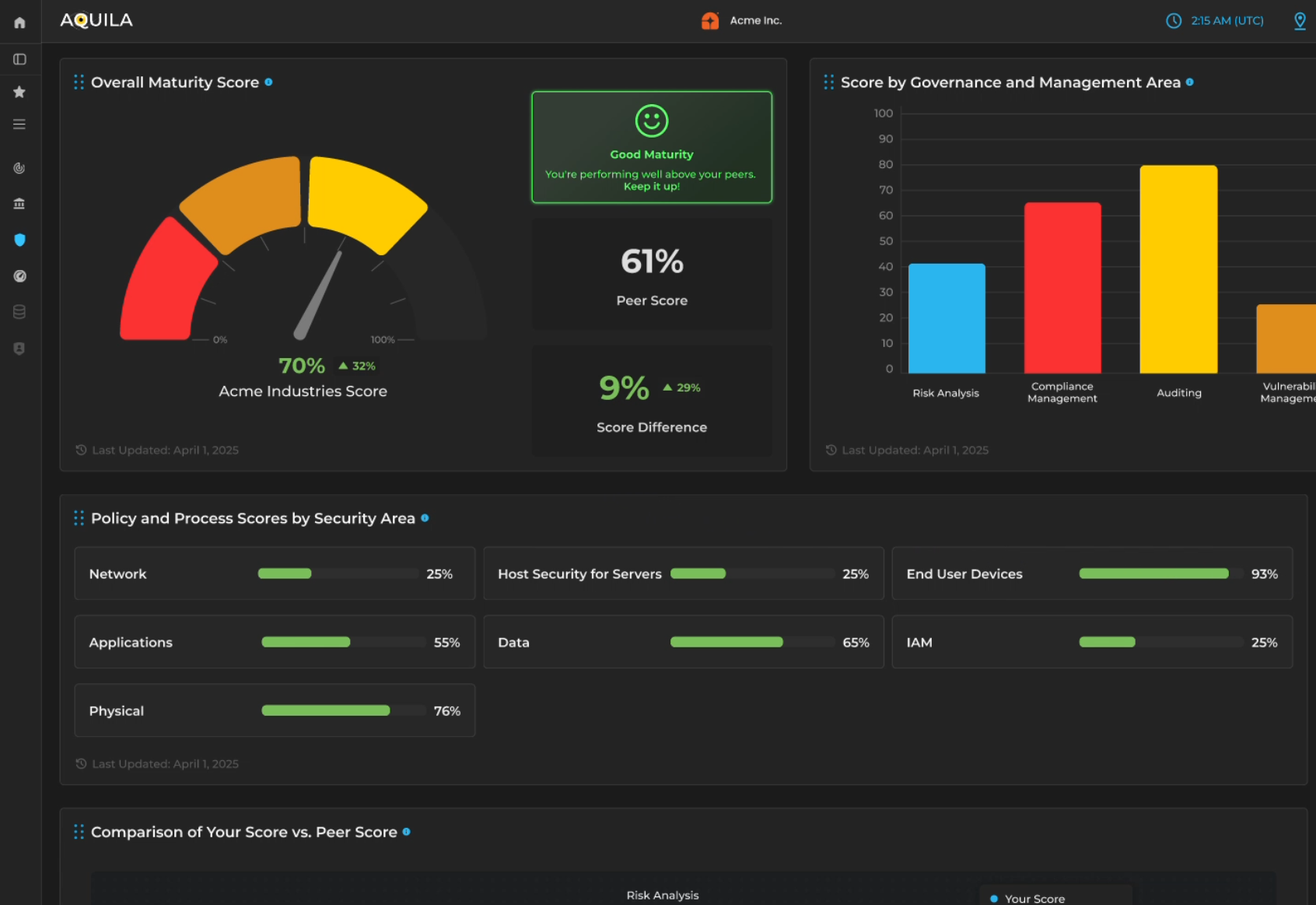
CyTech’s Cyber Maturity Benchmark gives organizations a clear, data-driven view of their cybersecurity posture compared to industry peers.
Working annually with over 1,000 CISOs worldwide, CyTech builds an industry-based benchmark across 34 industries and nearly 100 subindustries, offering unparalleled insights into sector-specific performance.
This empowers businesses to identify gaps in governance, risk management, and technical controls, prioritize improvements, and align with real-world standards, helping prevent waste, overconfidence, and confusion in security planning.
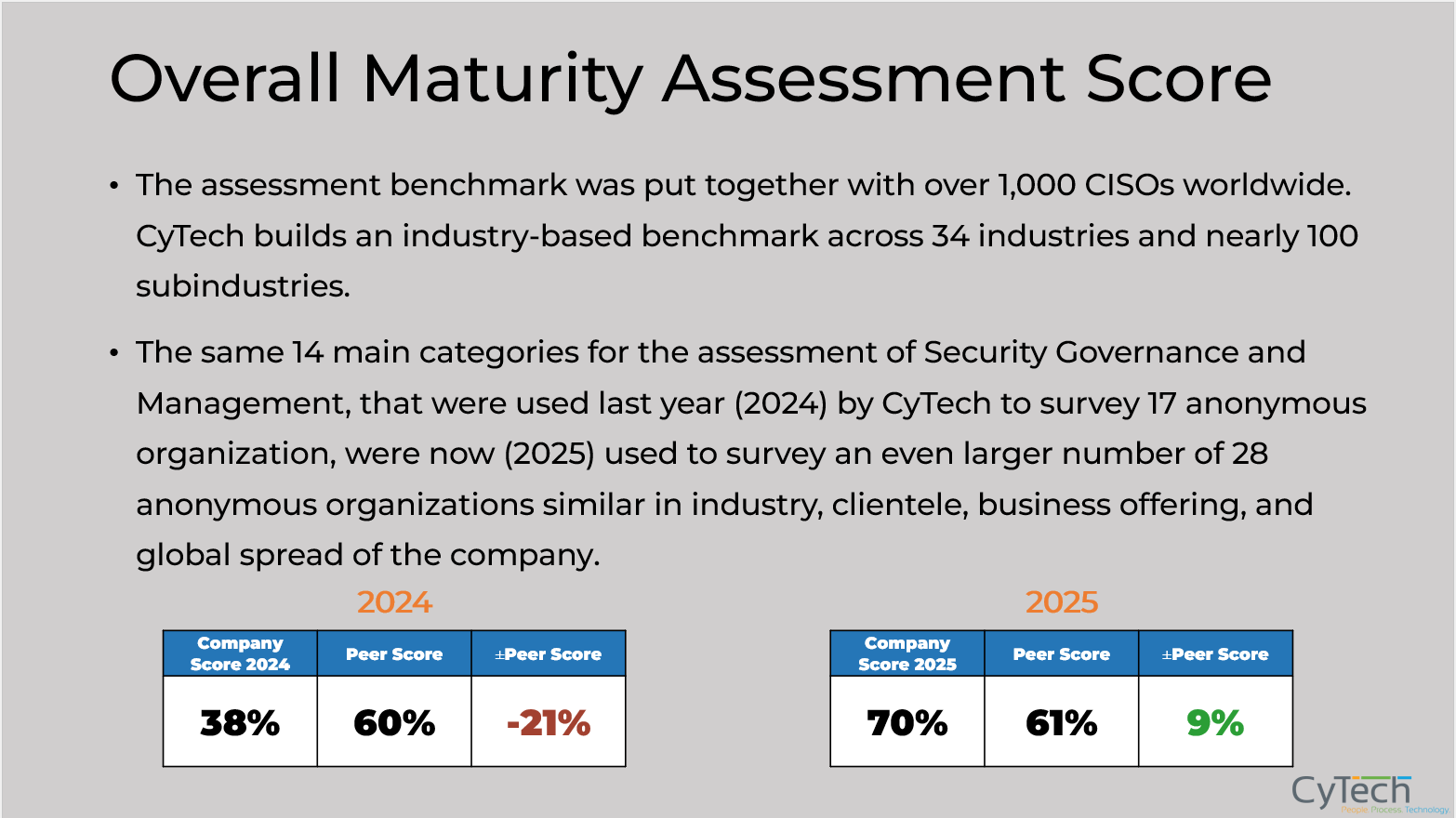
Many organizations struggle to determine whether their cybersecurity spending is sufficient or misaligned. CyTech’s framework helps quantify risk exposure and maturity across key domains, enabling businesses to allocate resources where they’ll have the greatest impact.
With AQUILA’s automated analytics and a deep understanding of peer investment trends, companies can track ROI, reduce redundant spending, and ensure their cybersecurity investments are both strategic and competitive.

Cyber threats and compliance requirements are constantly evolving. CyTech’s Cyber Maturity Benchmark supports continuous improvement by providing actionable insights and maturity scoring across frameworks like NIST, ISO 27001, and CMMC.
Combined with industry-specific benchmarking from thousands of global partners, this ensures organizations stay audit-ready, reduce regulatory risk, and build a resilient security culture that evolves with their threat landscape.
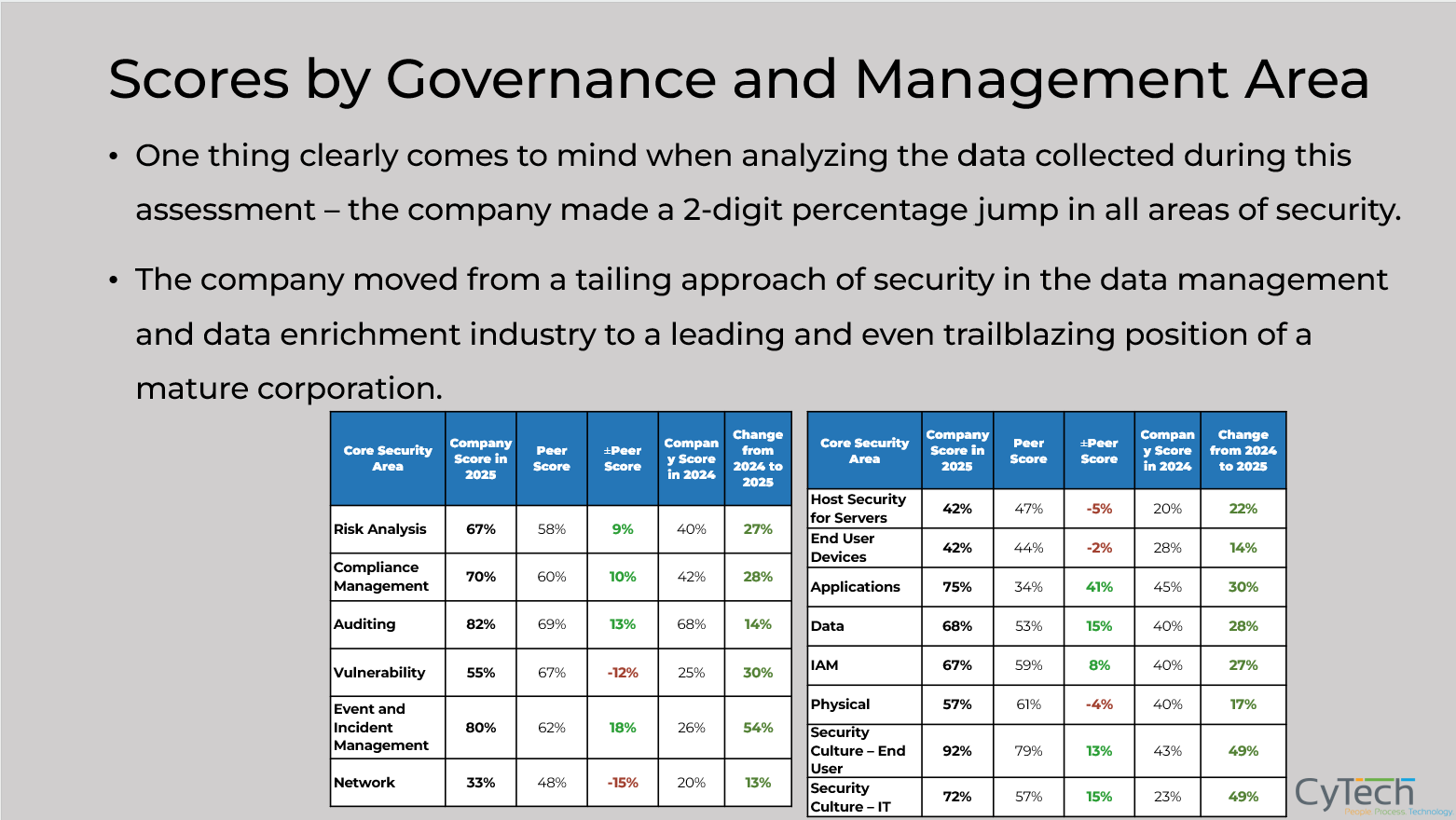
A mid-sized European logistics company was facing increasing pressure from clients and regulators to demonstrate cybersecurity readiness, but lacked a clear understanding of how its posture compared to industry peers.
The company partnered with CyTech to implement the Cyber Maturity Benchmark, gaining visibility into its strengths and weaknesses across governance, risk management, and technical controls.
By benchmarking against 34 industries and nearly 100 subindustries, and leveraging insights from over 1,000 CISOs worldwide, the company identified underperforming areas and reallocated its cybersecurity budget to address the most critical gaps.
Within six months, it improved its maturity score by 28%, aligned with ISO 27001 and NIS2, and confidently presented its progress to stakeholders, transforming cybersecurity from a compliance checkbox into a strategic advantage.
“When we first engaged CyTech, our cybersecurity posture was 22% behind our industry peers, a gap that left us vulnerable and uncertain about where to focus our efforts. The Cyber Maturity Benchmark gave us clarity we’d never had before.
With CyTech’s executive team guiding me as the CISO, we developed a strategic roadmap that aligned our security investments with real-world risks and peer benchmarks. Backed by CyTech’s data-driven analysis, we presented a bold proposal to our board: increase our cybersecurity budget from $6M to $11M. The benchmark insights were so compelling that the board approved it unanimously.
Within a year, the results were undeniable. Not only did we close the gap, we surpassed our peers and were ranked 10% higher than the industry average in overall cyber maturity.
CyTech didn’t just help us improve; they helped us lead. Their expertise, transparency, and strategic insight turned cybersecurity into a board-level success story.
We now use the Cyber Maturity Benchmark as a cornerstone of our annual planning cycle.”
Jason S., CISO
average improvement within the first year
restructured their budgets
say the benchmark helped them justify cybersecurity investments