The First Online Full Cybersecurity Suite
Built for real‑world resilience. Designed for global leaders.
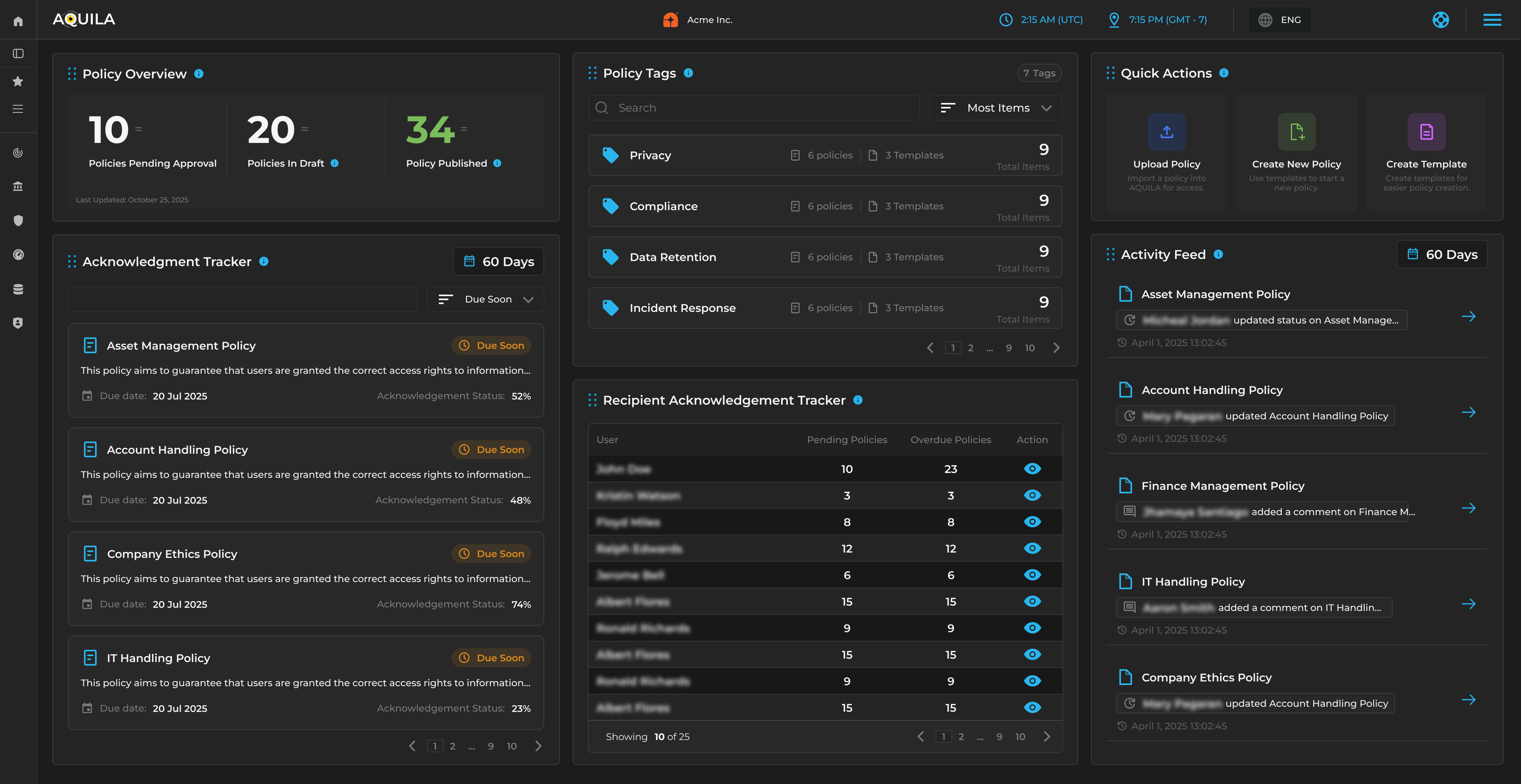
AQUILA is the world’s first online, fully integrated cybersecurity suite — a unified command system that gives CISOs clarity, control, and real‑time decision power across every domain of security.
Designed by Chen Heffer, AQUILA transforms fragmented operations into a disciplined, interconnected nervous system built for modern organizations.

A New Category
The unified operational layer that connects every domain of cybersecurity.
AQUILA introduces a new category in cybersecurity: the Cybersecurity Command System. It is not a tool, dashboard, or platform. It is the operational layer that unifies governance, risk, compliance, intelligence, engineering, identity, cloud, and resilience into one disciplined system.
Every domain communicates. Every signal converges. Every decision is informed. AQUILA replaces fragmentation with structure, noise with clarity, and complexity with a single, interconnected command environment built for modern security leaders.
![[team]](https://cdn.prod.website-files.com/6954708495d04649d41c9ddd/6955af3f3fba16e9d6e3c80d_3.jpeg)

![[interface] image of a computer showcasing educational software (for a edtech)](https://cdn.prod.website-files.com/image-generation-assets/4f03357b-3643-45d4-8090-85d1f1ea24e1.avif)
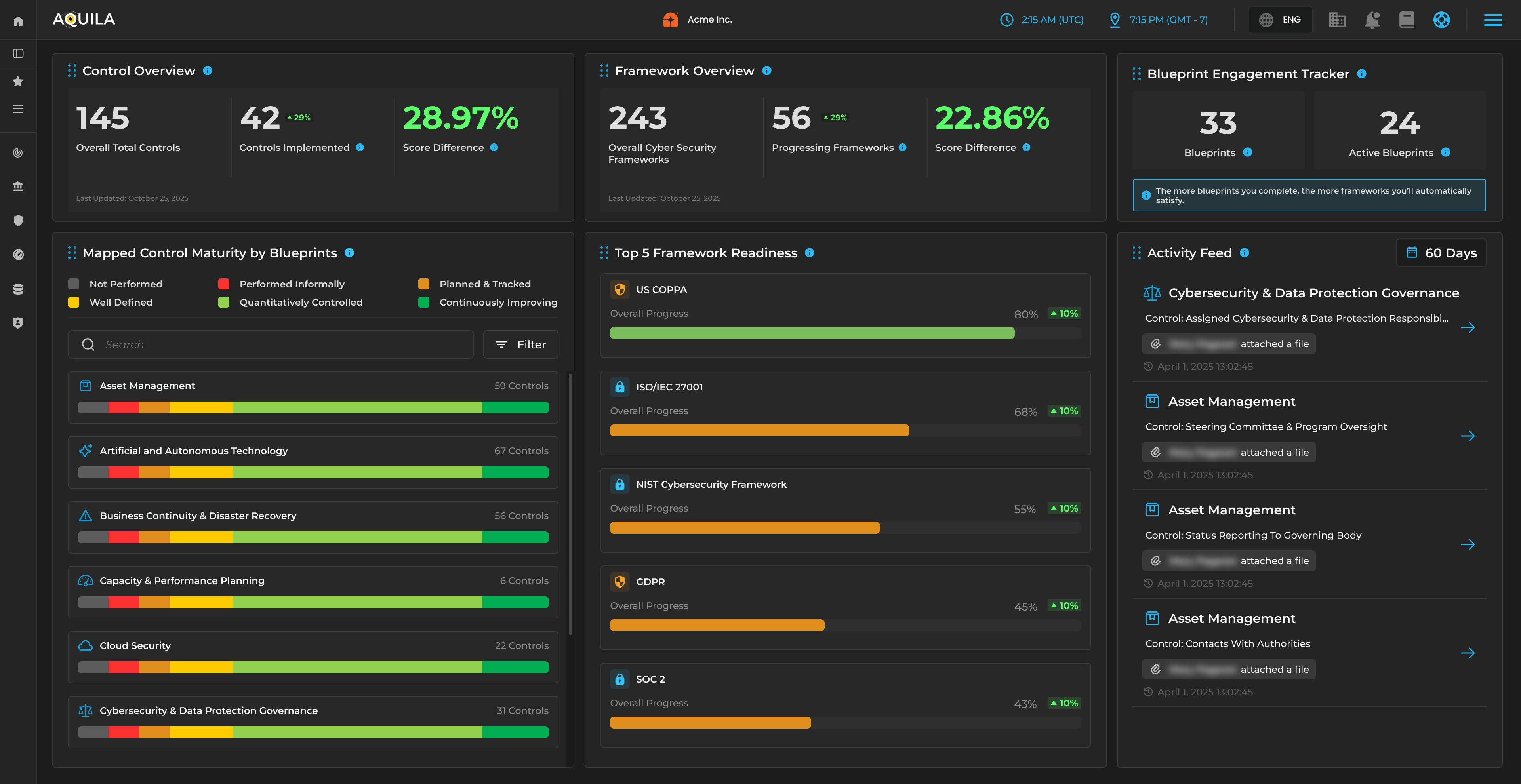
AQUILA’s Strategic Architecture
A disciplined, future‑ready structure built from years of real‑world CISO experience.
AQUILA’s architecture is built on ten strategic domains — each one evolved from the original six and expanded to meet the realities of 2026: AI regulation, cloud‑native ecosystems, supply chain exposure, board‑level accountability, and the rise of automation‑driven SOCs. These domains are not theoretical. They are mapped to real modules, real workflows, and real interoperability across the AQUILA system. Together, they form the backbone of the world’s first online full cybersecurity suite.
%20Dashboard.png)
Translates cybersecurity into language the board understands.
Focus:
KPIs, KRIs, dashboards, cyber annual workplans, ISSC, pressure analysis, and senior management involvement.
Elevates data security into mature data governance.
Focus:
Data discovery, classification, DSPM, DPIA, privacy compliance, and data security methodologies.
Keeps you ahead of NIS2, DORA, CIRCIA, CRA, AI Act, and more.
Focus:
UCB, compliance audits, security/privacy compliance, policies & procedures, and maturity assessments.
Secures your extended ecosystem and vendor landscape.
Focus:
SCRM, vendor questionnaires, CTI inputs, CRAM, and vulnerability management.
Builds a human resilience engine around your technology.
Focus:
Training & awareness, phishing simulations, charters, policies, org structure, and governance committees.
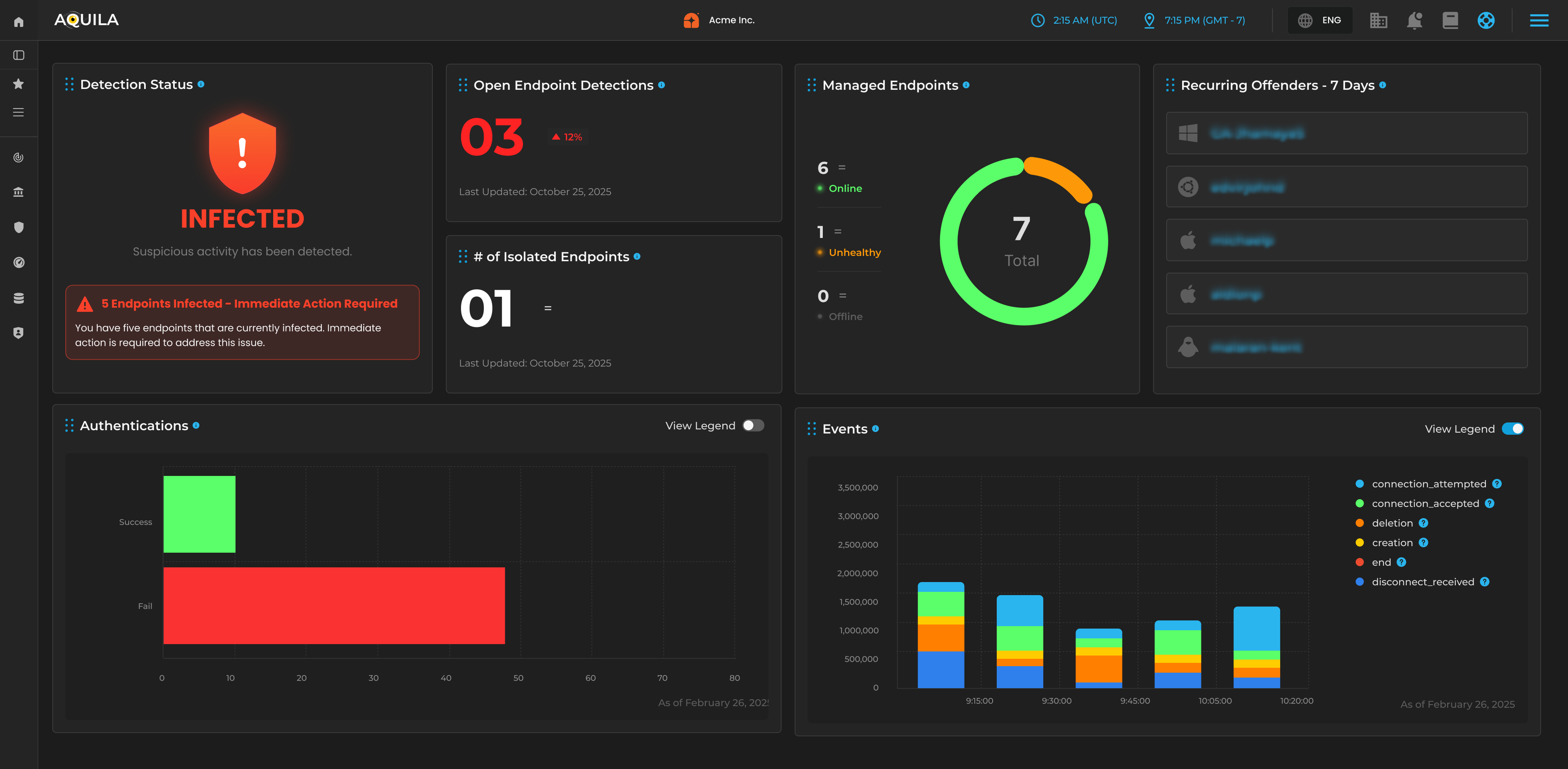
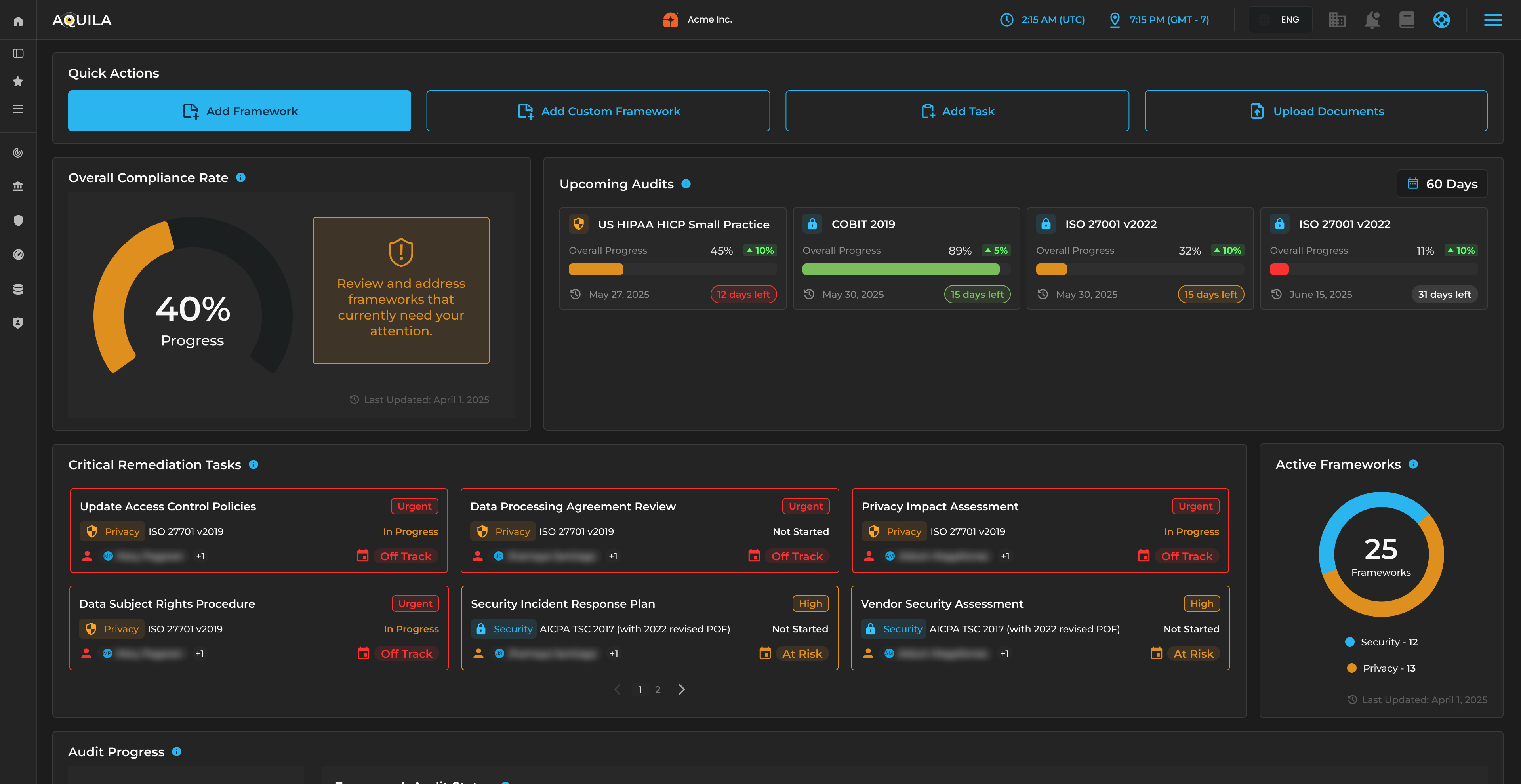
Drives lean, high‑performing SOCs with automation and AI.
Focus:
CIM, SOAR, EDR, UEBA, CTI enrichment, KRIs, and SOC KPIs.
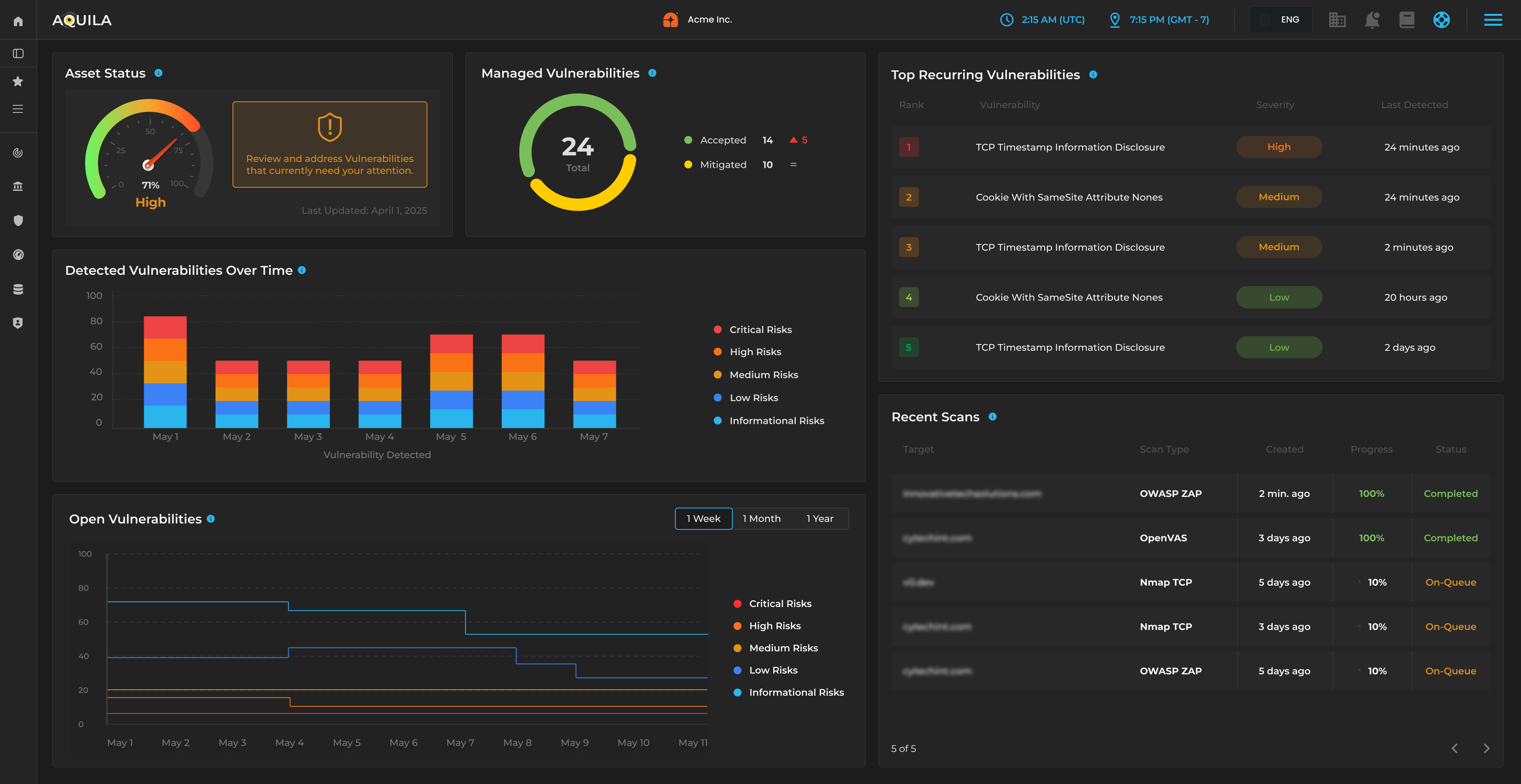
Addresses AI‑driven threats, synthetic data, and model governance.
Focus:
AI‑enabled CTI, AI analytics, risk scoring accuracy, and AI‑driven UEBA.
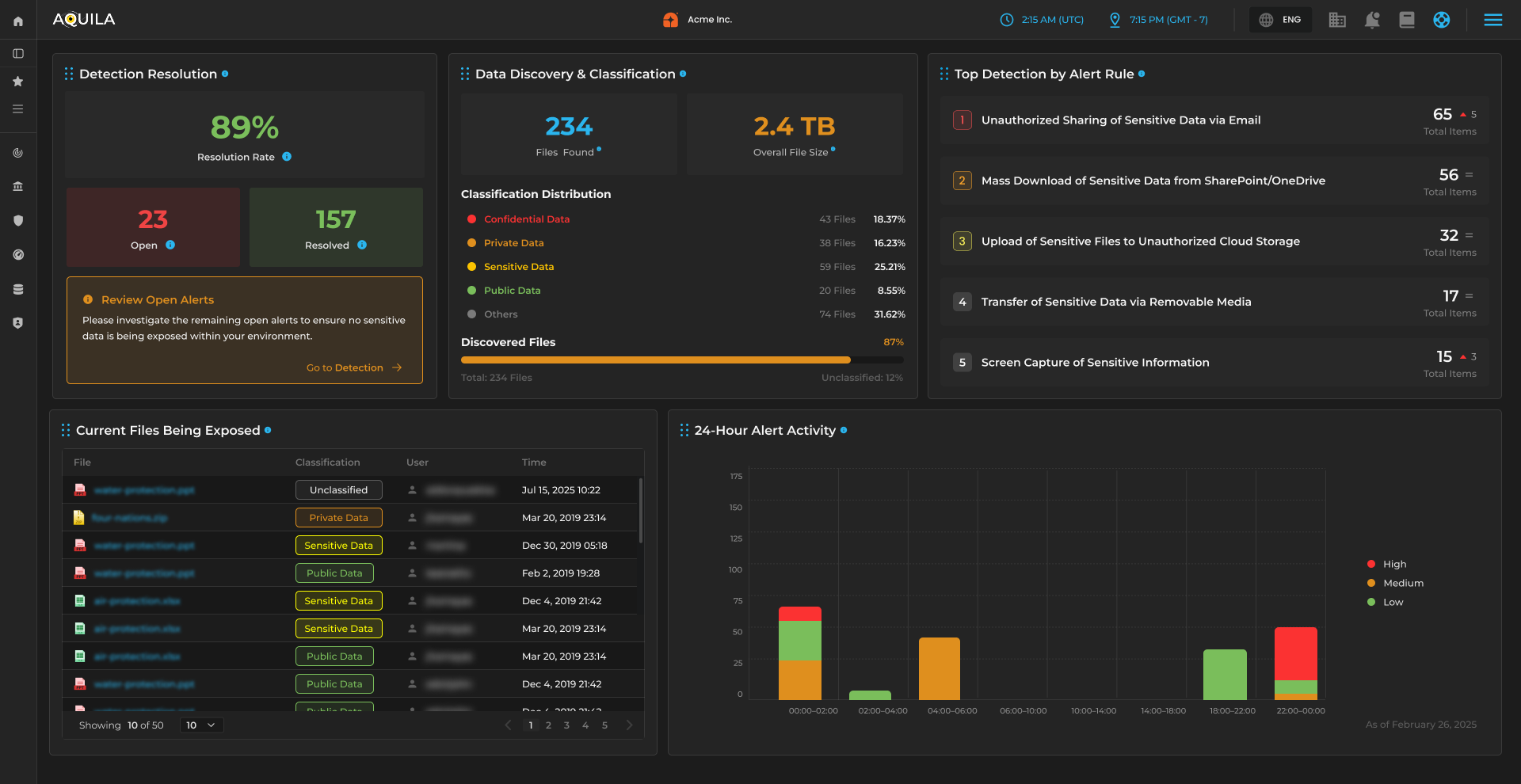
Secures multi‑cloud, SaaS, and API‑driven environments.
Focus:
CSPM, DSPM, IAM lifecycle, PIM, and remediation of cloud and data misconfigurations.
%20Dashboard.png)
Extends IAM into full zero trust coverage.
Focus:
IAM, MFA coverage, lifecycle workflows, IAM RACI, least privilege, and onboarding/offboarding integrity.

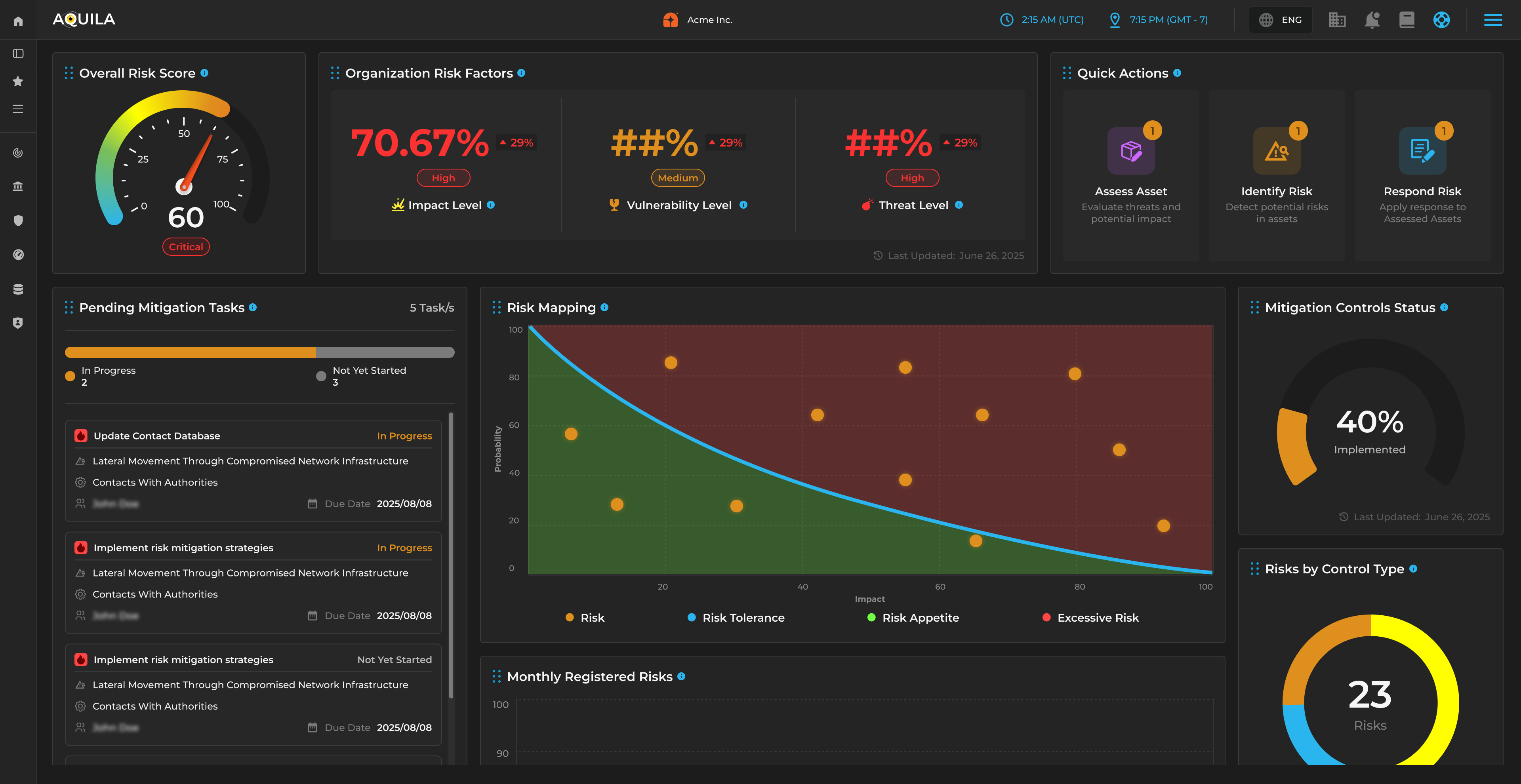
Ensures you can withstand, recover, and return to compliance.
Focus:
BIA, BCM, CRAM/CSRM, resilience exercises, and Return to Compliance (RtC) time.

Built With Purpose
AQUILA was born from real‑world leadership, not theory.
AQUILA was architected by Chen Heffer after decades of leading, mentoring, and certifying CISOs across the globe. It was built to solve the problems real security leaders face every day: fragmented tools, noisy dashboards, blind spots, and operational chaos.
AQUILA replaces that chaos with structure — a disciplined, interoperable command system that connects every domain of cybersecurity into one unified experience. It reflects the mindset of a founder who has lived the pressure, carried the responsibility, and built the systems that others now depend on.

From board reporting to SOC optimization — AQUILA gives every role the clarity it needs.
AQUILA is designed for real organizations with real complexity. Whether you’re a global CISO, a compliance director, a cloud architect, or a SOC manager, AQUILA gives you the structure, telemetry, and decision support you need to lead with confidence. Each domain is mapped to specific roles, workflows, and KPIs — so every leader sees what matters, acts with clarity, and contributes to a unified security posture.
CISO / Head of Security
All 10 domains
Unified command, board reporting, risk posture, strategic KPIs
Compliance Director
Regulatory Intelligence, Data Governance, Metrics
Audit readiness, framework mapping, evidence management
Cloud Architect
Cloud & API Security, Zero Trust Architecture
Multi-cloud posture, IAM lifecycle, segmentation enforcement
SOC Manager
Security Automation, AI Security, Threat Intelligence
CIM, SOAR, UEBA, CTI enrichment, SOC KPIs
Privacy Officer
Data Governance & Privacy, Compliance
DSPM, DPIA, classification, consent tracking
Risk Manager
Cyber Metrics, Third-Party Risk, Resilience
CRAM, CSRM, vendor scoring, BCM, RtC time
Training Lead / HR
Cyber Talent & Culture, Metrics
Training metrics, org structure, phishing simulations
Board / Executive Team
Cyber Metrics & Board Reporting
Strategic KPIs, KRIs, dashboards, ROI visibility
AQUILA gives leaders what every organization needs but no platform has ever delivered: structure, intelligence, and measurable control.

AQUILA replaces fragmented tools with a single, interconnected architecture.
Every domain, module, KPI, and workflow feeds into one intelligence core — giving leaders a complete, real‑time view of their entire security posture.

AQUILA’s domains are not theoretical. They are mapped to real modules, real KPIs, and real interoperability across the system — from board reporting and DSPM to SOAR, CTI, IAM, and BCM.
This is the only cybersecurity suite built on a CISO‑designed domain model.
![[interface] image of a computer showcasing educational software (for a edtech)](https://cdn.prod.website-files.com/image-generation-assets/4f03357b-3643-45d4-8090-85d1f1ea24e1.avif)
AQUILA translates cybersecurity into business language.
KPIs, KRIs, dashboards, and board‑ready summaries are generated automatically — giving executives clarity without noise, and CISOs the visibility they’ve always needed.
![[interface] image of a computer showcasing educational software (for a edtech)](https://cdn.prod.website-files.com/6954708495d04649d41c9ddd/69553e9a9da841dbe1ca7d99_Hands%20on%20Tablet%202.jpeg)
AQUILA uses AI where it matters:
• UEBA
• CTI enrichment
• Risk scoring accuracy
• Anomaly detection
• SOC triage
• Cloud posture analysis
• Data exposure detection
AI is not a feature — it’s embedded into the system’s nervous layer.
![[interface] image of a computer showcasing educational software (for a edtech)](https://cdn.prod.website-files.com/6954708495d04649d41c9ddd/6954732b823a9ec77d4ef6f2_5e6823a6-fda2-44da-b1f8-1daafdde47c2.avif)
Every module in AQUILA feeds another.
Risk informs BCM.
DSPM informs IAM.
CTI enriches SOAR.
KRIs feed CRAM.
Vendor scoring feeds compliance.
Training metrics feed governance.
This is the opposite of a siloed platform — it’s a living system.
![[interface] image of a computer showcasing educational software (for a edtech)](https://cdn.prod.website-files.com/6954708495d04649d41c9ddd/69587f88ca5fc1e3794d3617_3.jpeg)
AQUILA reflects the pressures, responsibilities, and decision patterns of real security leaders.
It was built by someone who has lived the role — not by product managers guessing what CISOs need.
This is founder‑led cybersecurity.
![[interface] image of a computer showcasing educational software (for a edtech)](https://cdn.prod.website-files.com/6954708495d04649d41c9ddd/69587fde4882cd139637796b_2.jpeg)
AQUILA is built for the regulatory, AI, cloud, and supply chain realities of the next decade:
• NIS2
• DORA
• CIRCIA
• CRA
• AI Act
• multi‑cloud ecosystems
• API‑driven architectures
• AI‑enabled threats
AQUILA evolves as the world evolves.
AQUILA turns complexity into clarity — giving leaders the confidence to act, not react.

No more jumping between tools, dashboards, or spreadsheets.
AQUILA gives you a single, unified view of your entire cybersecurity posture — mapped across the 10 strategic domains, updated in real time, and interpreted through the intelligence core.
It feels like switching on the lights in a room you’ve been navigating in the dark.

AQUILA gives you the KPIs, KRIs, and executive‑grade summaries you need to speak the language of the board.
No noise.
No clutter.
Just clarity, direction, and measurable progress.
It feels like having a command center built for leadership, not technicians.
![[interface] image of a computer showcasing educational software (for a edtech)](https://cdn.prod.website-files.com/6954708495d04649d41c9ddd/6958816d9226a001db6bf382_2.jpeg)
AQUILA correlates signals across domains — risk, cloud, identity, compliance, AI, SOC, supply chain — and surfaces what matters most.
You don’t hunt for insights. They come to you.
It feels like having a second brain dedicated to cybersecurity.
![[interface] image of a computer showcasing educational software (for a edtech)](https://cdn.prod.website-files.com/6954708495d04649d41c9ddd/695881e9c16b04d6474c3ac1_Cyber%20Threat%20Intelligence%20(CTI).jpeg)
AQUILA’s automation, AI analytics, and interoperability reduce manual work, eliminate blind spots, and prevent issues before they escalate.
It feels like moving from reactive security to proactive leadership.
![[interface] image of a computer showcasing educational software (for a edtech)](https://cdn.prod.website-files.com/6954708495d04649d41c9ddd/69588264130ea1bbe29580ae_4.jpeg)
AQUILA doesn’t just measure technology — it measures people, culture, governance, and resilience.
It gives you the tools to build a security program that grows with your business.
It feels like leading a mature, disciplined, future‑ready security organization.
A System Built With Discipline
AQUILA is built as a modular, interoperable system where every component feeds another.
Each module produces KPIs, consumes upstream inputs, and generates downstream outputs — all interpreted through the AQUILA Intelligence Core.
This is not a platform. It is a cybersecurity operating system.

![[interface] image of a computer showcasing educational software (for a edtech)](https://cdn.prod.website-files.com/image-generation-assets/8056605e-9b3e-431f-9e2f-1ec8709d90c7.avif)
Each of the 10 strategic domains contains a set of modules.
Each module produces measurable KPIs.
Each KPI rolls up into domain‑level performance.
Modules feed structured signals into the intelligence core, including:
• Risk scores
• Cloud posture
• IAM lifecycle events
• DSPM findings
• CTI enrichment
• Compliance
(etc.)
The intelligence core correlates these signals across domains.
The intelligence core then feeds:
• CRAM (risk scoring)
• CSRM (risk management)
• BCM (resilience)
• Compliance dashboards
• SOC workflows
• IAM workflows
• Cloud remediation
• Board reporting
(etc.)
This is where AQUILA becomes a decision engine, not a dashboard.